A recent warning has been issued to millions of Android users regarding new malware. Named “Brokewell”, this malware disguises itself as a regular application but, once installed, it collects the phone owner’s personal data and may allow attackers to take remote control of the Android device. The malware can also track users and access banking applications.

The malware has been found on Android devices
To avoid detection, the “Brokewell” app containing the malware is disguised as an update for a new version of Google Chrome. To make it even more convincing, it is designed to look like a Chrome installation prompt.
If a user installs “Brokewell” on their phone, the malware can “log accessibility events” and collect all touch gestures, swipes, data entry, or information displayed on the phone. This data is then sent to the hacker’s server and can be used to steal information, take remote control of the phone, or even drain bank accounts.

The malware disguises itself as a Google Chrome update, so users may install it unknowingly.
According to ThreatFabric, a Dutch security company, this malware is extremely dangerous. “Brokewell poses a significant threat to the banking industry, providing attackers with remote access to all assets available through mobile banking”, the security company said.
ThreatFabric also traced the malware to a hacker named Baron Samedit Marais, who is believed to be selling it along with a range of other malicious tools through a website called Brokewell Cyber Labs.
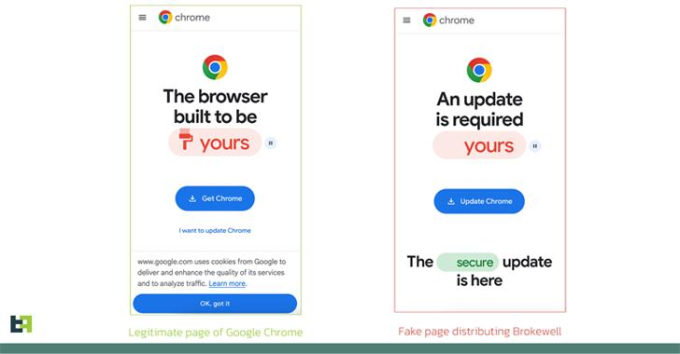
The real Chrome update notification (left) and the fake notification containing the malware (right) have subtle differences.
According to PhoneArena, Google stated that users can ensure their safety by using a feature available on Google Play: “Android users are automatically protected from known versions of this malware by Google Play Protect, which is turned on by default on Android devices with Google Play Services. Google Play Protect can warn users or block apps that are known to exhibit malicious behavior, even if they are installed from sources other than Play.”