“CyberWar Insider” is a program that shares cybersecurity stories from the perspective and practical experience of insiders who are engaged in the daily battle against cyber threats. The program is organized by Viettel Cyber Security (VCS), aiming to disseminate valuable lessons and practical knowledge to foster a safer online environment.
With the rise in ransomware attacks, the first edition of CyberWar Insider focused on the theme “Unlocking the Story of Ransomware.” During the nearly two-hour conversation, led by Mr. Nguyen Xuan Nam, VCS’s Strategy Director, nearly 300 attendees heard fascinating stories shared by experienced ransomware incident handlers: Mr. Nguyen Cong Cuong, Director of the Monitoring and Response Center for Cyber Space (VCS), and Mr. Tran Minh Quang, Director of the Center for Analysis and Sharing of Cyber Security Risks (VCS).
Untold Stories from the Ransomware Battle
“Whenever we receive a mission, my team and I often prepare for battle and remember to bring a blanket,” said Mr. Nguyen Cong Cuong as he began his conversation at CyberWar Insider. He explained that when data encryption attacks impact the infrastructure, it is often necessary to intervene and fix the issue directly in the server room, which can be very cold. Working in such an environment for several consecutive days has made a blanket an essential item. “Especially in the last six months, the number and frequency of encryption attacks on Vietnam’s infrastructure have increased, causing more severe losses,” he added.

Mr. Nguyen Cong Cuong shares insights into the challenges businesses face when dealing with Ransomware.
Ransomware attacks not only disrupt services but also impact the finances and reputation of businesses, leading them to prioritize quick system recovery without fully considering the potential risks of lingering hackers in their systems.
During nights spent resolving incidents, VCS experts often had to convince businesses to incorporate cybersecurity controls into the system restoration process, even if it meant a longer recovery time. “I shared with them that no one wants to spend days rebuilding a system only to have it compromised again a day or two later. Fortunately, the businesses understood and agreed,” said Mr. Cuong.
Mistakes That Cost Businesses Dearly in the Face of Ransomware
According to Mr. Tran Minh Quang, the ransomware trend in the last two years has combined with targeted APT attacks. Attackers are willing to lurk for extended periods, ranging from six months to a year, to gain access to critical data. While this presents a challenge, it also offers an opportunity for early detection. “The lack of monitoring tools or periodic ‘sweeps’ has caused businesses to miss out on opportunities to prevent attacks,” said Mr. Quang.

Mr. Nguyen Cong Cuong (left) and Mr. Tran Minh Quang (right)
Mr. Nguyen Cong Cuong highlighted two significant issues faced by organizations: privileged account management and network connections. Privileged accounts, similar to the keys to a house, are the most sought-after entry point for hackers as they can bypass monitoring systems. However, many businesses are using these accounts without proper control, logging in from multiple locations for various tasks, increasing the risk of exposure. “In every ransomware incident I’ve handled, there has been an issue with privileged account management,” he said.
While some units have established proper segmentation and firewalls to prevent the spread of intruders within their systems, they have inadvertently created favorable conditions for hackers by connecting these segments during operation, allowing them to connect and infiltrate from anywhere.
Response Strategies for Businesses
Driven by profit, attack groups are willing to invest to maximize their gains. Ransomware has evolved beyond mere malware into a Ransomware-as-a-Service (RaaS) industry. According to Viettel Threat Intelligence, ransomware attacks increased by 70% in Q1 2024 compared to the same period in 2023.
Mr. Tran Minh Quang emphasized that businesses still have a chance to recover if they have a backup. This requires implementing appropriate backup procedures and adopting the 3-2-1 backup rule to ensure maximum data security. Additionally, encryption usually occurs in the final stage of an attack after a prolonged period of lurking. The most critical factor is early risk detection to enable timely mitigation. The ideal approach is to monitor continuously or, at the very least, conduct checks every three to six months given the current situation.

Mr. Nguyen Xuan Nam suggests that businesses need to implement strict privileged access management.
Based on recent attack trends, Mr. Nguyen Xuan Nam recommended that businesses strictly manage the storage of privileged accounts. “Privileged Access Management (PAM) solutions are already being used by many businesses and have proven effective,” said Mr. Nam, revealing that VCS is integrating PAM into its cybersecurity product and service ecosystem. This integration will enable businesses to implement rigorous and efficient privileged account management, effectively blocking external intruders from accessing their systems.
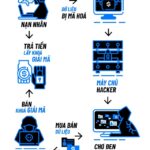
Over 37,000 dual ransomware attacks on Tet holiday, 83,000 people fell victim, urgent warning from experts
According to cybersecurity experts, dual ransomware is a form of attack that is highly “terrorizing” to its victims. The victims are forced to pay a ransom in order to “redeem” their data decryption key.
Silent Sitting: Phone Hack Gives Control and Drains Bank Accounts – Protect Your Safety
In recent times, there have been numerous cases where individuals have raised concerns about their phones being hijacked and, within a few hours, their bank accounts being depleted. Even more concerning is the fact that some users have not performed any actions, yet money still disappears from their bank accounts. According to cybersecurity experts, anyone can become a victim.