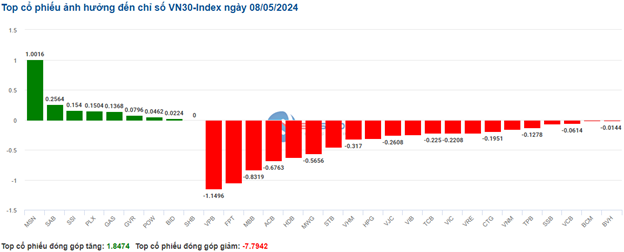
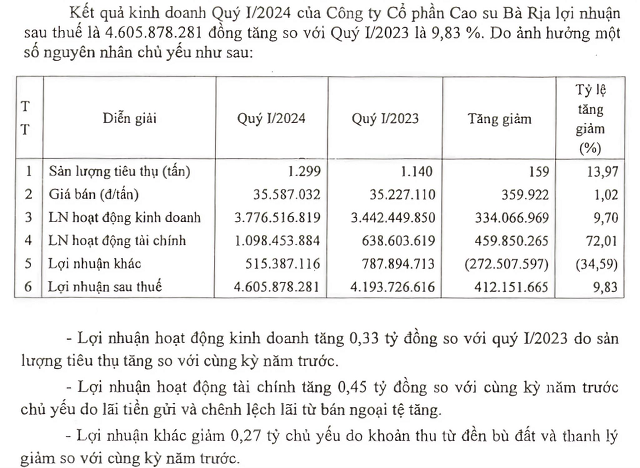
Cybercriminals Target Developing Countries as Testing Grounds for Malware
According to a new report released by cybersecurity firm Performanceanta and reported by the Financial Times, hackers are increasingly adopting the “stepping stone” strategy of infiltrating low-income countries’ systems before moving on to more high-profile targets in North America and Europe.
BUSINESSES WORLDWIDE HAVE LOST NEARLY $28 BILLION SINCE 2020 DUE TO CYBER INCIDENTS
“Hackers are testing the waters in the weaker security environments of developing nations to test the quality of their malware before targeting wealthier nations,” Performanceanta said.
The International Monetary Fund (IMF) reported in April that cyberattacks have almost doubled globally since before the COVID-19 pandemic, with developing nations experiencing a sharper rise due to their rapid digitalization and improved internet connectivity coupled with “deficient” defenses.
The IMF noted that cyber incidents have cost businesses worldwide nearly $28 billion since 2020, with billions of records stolen or compromised, adding that the total cost is likely “substantially higher.”
Nadir Izrael, CTO of cybersecurity firm Armis, said that developing nations provide a low-risk environment for cybercriminals to operate in due to companies in these countries often having weaker cybersecurity awareness.
“Let’s say they wanted to go after banks,” Izrael told the Financial Times. “They might go and try a new payload in a country like Senegal or Brazil, where there’s a lot of banking or companies that are international branches of the same type of thing they ultimately want to go after.”
Performanceanta’s report notes that Medusa, a prolific ransomware gang, has been “turning files to stone” by stealing and encrypting corporate data, with its initial attacks in 2023 targeting businesses in South Africa, Senegal, and Tonga. Medusa was also responsible for 99 breaches in the U.S., U.K., Canada, Italy, and France last year.

Earlier, personal data of citizens of Betton, a town in the metropolitan area of Rennes, France, was leaked on Medusa’s dark web portal. The town suffered a ransomware attack in late August 2023 and refused to pay the $100,000 ransom demanded by hackers. In response, the cybercriminals publicly released a database containing personal information such as identity documents, addresses, and administrative exchanges on the dark web.
Medusa attacks both individuals and organizations, with Hanah-Marie Darley, director of threat research at cybersecurity firm Darktrace, explaining that security teams within organizations will receive alerts about a pending attack. However, regular users will typically only become aware of an attack when they are locked out of their computer systems.
A file is then dropped with the !!!READ_ME_MEDUSA!!!.txt., which instructs users to log on to a dark web portal and begin negotiating a ransom payment with a “customer service” representative. Should victims refuse, the attackers threaten to publish the stolen data.
INTERNATIONAL CRIMINAL GROUPS ARE RESELLING TECHNOLOGY TO CRIMINALS IN DEVELOPING COUNTRIES
Cybersecurity companies are monitoring dark web marketplaces for information and subsequently setting up “honeypots” – fake websites mimicking targets often targeted by cybercriminals in developing countries – to act as decoys to detect test attacks early on.
The CTO of cybersecurity firm Armis said that one group of attackers was observed discussing a new vulnerability, tracked as CVE-2024-29201, earlier this year, “targeting a number of exposed servers in third-world countries to test the reliability of the exploit.” His analysts monitor the group’s communications on the dark web.
Through its use of honeypots, Armis later confirmed the suspicion: this group only attacked targets in Southeast Asia, using the techniques more broadly only at a later stage. Microsoft’s director of threat intelligence strategy, Sherrod DeGrippo, has noted smaller-scale attackers in developing countries are acquiring lower-cost ransomware and carrying out their own small-scale attacks.
According to Darktrace’s Darley, hacker groups like Medusa have started selling their creations to smaller-scale attackers. She explains that while these less sophisticated attackers may not fully understand how the technology works, they are using it to target highly vulnerable small organizations.
CYBERCRIMINALS ARE INCREASINGLY SANDBOXING TECHNIQUES IN DEVELOPING NATIONS
Darley stresses that any attacker who takes the time to “sandbox their techniques” in less-developed areas will inevitably become more sophisticated over time.
Teresa Walsh, director of global threat intelligence at financial sector intelligence-sharing organization FS-ISAC, said that hacker groups will work in local environments to “perfect” their methods, then “export” their schemes to countries that may share a common language, such as from Brazil to Portugal.
Brendan Kotze, network analyst at Performanceanta, notes that the pace of digital adoption in Africa is “outstripping the development of robust cybersecurity measures, while awareness of cyber threats generally remains low.” He adds, “Together, this creates an increasingly concerning gap in defenses that cybercriminals are exploiting.”